4 ways to identify fraudulent transactions to steal accounts and money
(Baonghean.vn) - To protect yourself from online fraud or scams, users should equip themselves with knowledge to recognize and prevent... Below are some common forms of online fraud today and how to recognize and prevent them.
1. Email scams
Common contents of scam emails are: notification that the user has won a prize, notification that the bank account has been locked, notification of credit card transactions, requesting the user to provide personal information...
 |
How to recognize scam emails
Phishing emails used by hackers are very diverse. Here are some common signs to recognize:
- Require users to provide personal information and access account information.
- Provide information about awards and events to users.
- News related to hot issues in society at the present time.
- Send attachments related to work, recruitment or information about fields that users are interested in.
- The email only contains images. Clicking on any area of the image or email may lead to a fake website that tricks users into entering personal information or infects them with malware.
- The email contains a lot of unusual bold information to attract the user's attention.
- A letter with general greetings and introductions without addressing the recipient specifically. Usually begins with “hello”, “hello”, “Dear Friend”….
- Submit an HTML file with the form of payment login page, bank, famous website.
How to prevent
For every email received, users need to carefully check the sender's address. Usually, phishing email addresses will be forged to closely resemble an email address that the user trusts.
Never reply to emails sent from overseas that ask for help transferring money, promise a fee, but also ask the user to send bank account information to pay additional fees.
Do not click on any links or open any attachments if you do not know the sender or have not checked them with antivirus tools.
Notify your service provider and delete the scam emails from your mailbox; inform your colleagues, friends, relatives and everyone about this email and similar scams to avoid them.
2. Fraud through fake websites
Usually, bank account hijacking scams are carried out through emails, forums or social networks. Hackers will send fake bank scam emails to notify users to update personal information or notify of unusual transactions.
These emails will have a link to the bank's fake website. When the user visits the fraudulent website and logs in, all the information will be sent to the hacker.
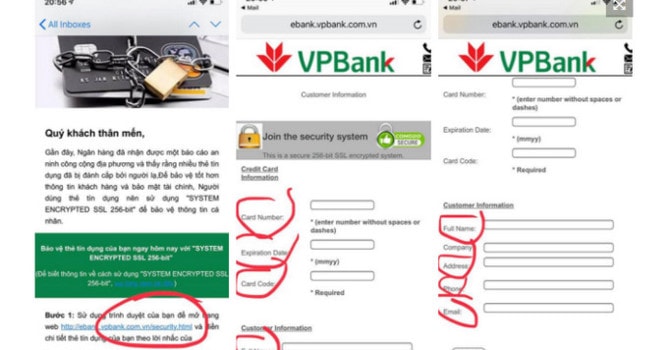 |
How to identify fake websites
Emails, forum posts or social media posts with the following content may be scams:
- Suspicious email address. Usually uses a domain name that is similar to the user's legitimate bank, such as:[email protected](missing letter o, or replace letter o with number 0).
- The initial greeting does not use a specific username but displays: “Dear customer”. However, in some cases, the username may be used if the hacker has gathered enough information.
- Link addresses are incorrect or intentionally hidden.
- The email is an emergency notification, if not acted upon immediately, the account will be taken over. The bank will not be liable for the user's account if you ignore this email.
How to prevent
The only way to avoid this is to never click on bank links sent in emails, forums or social networks. Type the bank's website address directly into the browser address bar.
3. Social media scams
 |
To trick users, hackers will send messages or write posts on users' personal pages with content enticing readers to click on links containing malicious code. When accessing the phishing links, users are instructed to enter their email address or phone number, password and answer to security questions.
This information will then be sent directly to the hacker. Even in case the user is suspicious and intentionally types the wrong username and password to check the legitimacy of the verification, this website will display a fake error message. Thereby, the user will confidently declare his personal information.
When re-entering the information a second time, the victim will be asked to wait 24 hours for confirmation. During that time, the hacker can access the victim's account or sell the account to bad guys for other purposes...
How to recognize social media scams
- When accessing a phishing site, it will often ask for additional steps, such as allowing additional functionality or re-sharing the message.
- Shocking or curious content.
- Promises things that social networking sites don't have or never do (see who visits the most, who are your closest friends…).
Prevention
- Research the app or article before accessing and installing it by using the phrase “app-name/ad-content-scam”. For example: “who views your wall the most - scam”.
- Learn about the social networking site's features to know what functions the provider has and what suspicious functions hackers can exploit.
- Check the access rights of applications on social networks, especially pay attention to access rights to personal information, permission to write on friends' pages, send messages to friends...
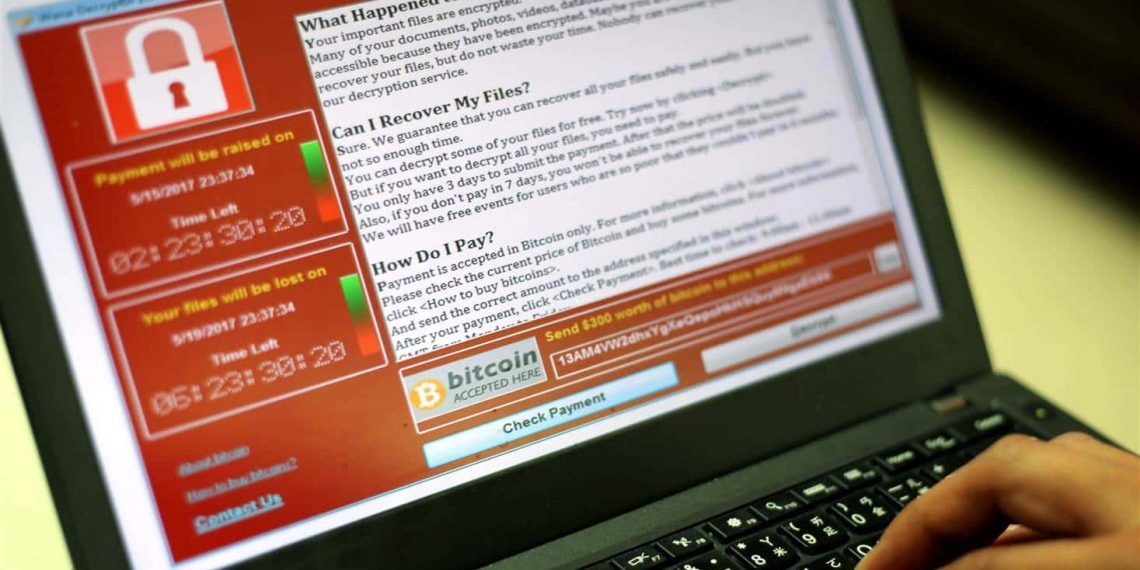
4. Ransomware
Ransomware can infiltrate users' computers when using cracked software, accessing the dark web, accessing fake websites, downloading and installing software of unknown origin, downloading attachments via spam emails, etc.
There are two common types of ransomware:Screen Lock Ransomware (Will lock your computer, display a message that the computer will be locked until a fine is paid);File Encryption Ransomware (Encrypts user's files, displays a message that the file has been encrypted, and asks the user to pay within a period of time before the ransom is increased).
 |
How to prevent
- Do not open suspicious emails or attachments.
- Always update your browser and antivirus software.
- To limit loss, it is necessary to regularly back up important data to external hard drives or cloud storage services.
How to deal with ransomware infection
How to handle it depends on the type of ransomware and your computer's operating system, but the key step is to disconnect from the network to limit the spread.
For lock screen ransomware: Run your anti-malware software to remove the ransomware, or at least get instructions to remove it.
With file-encrypting ransomware: If important images, videos, spreadsheets or documents have been securely backed up, users do not need to pay hackers, but only need to scan with anti-malware software and restore the backup on the computer.
In case there is no backup and all files are encrypted, for certain ransomware there are tools to recover data. Users should contact the information security department for assistance.

