Encryption technology: terrorism's new weapon
(Baonghean.vn) - Many officials in the Obama administration confirmed that the Islamic State (IS) has used a variety of encryption technologies for more than a year. Some of the best technologies are free, easily accessible applications such as Signal, Wickr and Telegram, which have the function of encrypting messages from mobile phones.
These officials implicitly imply that other encryption technologies are not as secure as terrorists and criminals think, and they clearly don't want them guessing which technologies are within the NSA's “penetration” capabilities.
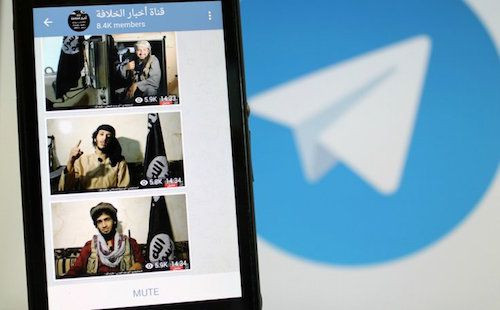 |
| Caption: IS channel on Telegram - one of the terrorist organization's "favorite" encrypted messaging apps. Photo: Internet |
Two weeks ago, ISIS used Telegram to claim responsibility for the downing of a Russian airliner over the Sinai Peninsula, killing 224 people. They used the app again last week to claim responsibility for the Paris massacre, in Arabic, English and French.
It’s unclear whether they used Telegram’s secure messaging service to encrypt their private conversations. It’s possible the Paris attackers met in person to plan the attack, especially since some of them lived in the same neighborhood in Brussels. But if there was a command center in Syria or elsewhere, some form of communication would have been needed.
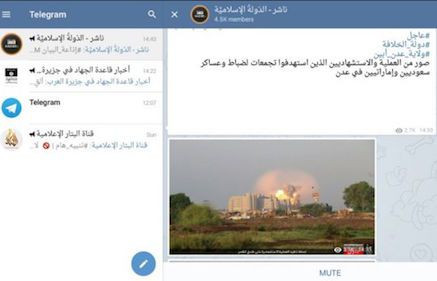 |
| IS used Telegram to issue statements claiming responsibility for the attacks. Photo: Internet |
The attack has reignited a bitter debate between US intelligence and Silicon Valley over end-to-end encryption. Just a week ago, the issue seemed to have been temporarily settled when President Obama said that forcing technology companies to hand over the keys to decrypt protected conversations and data was ineffective.
Apple has now made encryption a standard part of its iMessage messaging service. Apple CEO Timothy D. Cook has staunchly defended the technology, which holds the keys to decrypt messages between users at both ends of a conversation.
Mr. Cook argued to Mr. Obama that only by doing so can he convince customers that the most important data they store on their phones cannot be accessed by cybercriminals or other nations through hacking or by court order.
Mr. Cook said investigators have many ways to gather important clues from “metadata” about phone users, from information on the Internet cloud or by hacking into a target’s device.
But the speed of the encryption wave has raised alarm bells among law enforcement and intelligence officials. British Prime Minister David Cameron threatened late last year to ban such technology, but later backed down.
“I think this will open a whole new debate about security and privacy,” said Michael Morell, former Deputy Director of the Central Intelligence Agency (CIA).
“We’ve had a public debate about Edward Snowden,” the former NSA employee who leaked information about the agency’s efforts to crack encryption, he told CBS over the weekend. Mr. Morell said a new debate would be “caused by what happened in Paris.”
Shortly before the Paris incident, Belgian authorities confirmed that IS terrorists were hiding their communications through the use of online gaming tools such as Sony's PlayStation 4.
“It is even harder to track PlayStation 4 than WhatsApp,” Belgium’s interior minister, Jan Jambon, told the public last week.
 |
| Terrorists in Paris are believed to have exchanged information via Sony's Play Station Network. Photo: Internet |
Security experts counter that even user-to-user encryption leaves out a lot of data that could help determine who is talking to whom, where, and when. Matt Blaze, a computer security expert at the University of Pennsylvania, asserts:
“Encryption is effective at making it difficult to access the content of a communication, but it is not effective at hiding the existence of the communication.”
“All the encryption technology in the world is useless if the endpoint holding the decryption key is compromised. So it’s worth taking a second look at the idea that encryption makes terrorist communications completely secret.”
Even as Apple and other US companies are forced to weaken the encryption on their services, US authorities still have no legal authority over Telegram, the German messaging service that IS has recently used to spread its communiques.
Thu Giang
(According to NYTimes)
| RELATED NEWS |
|---|






