Google warns smartphone users to immediately turn off this setting to protect themselves from scam messages.
To avoid falling victim to phishing attacks, Google warns smartphone users to immediately disable a familiar feature that poses many security risks.
Google has just issued an important security warning for smartphone users, and it's something you shouldn't take lightly. The first reason is because it comes from Google itself. The second, and more worrying, reason is that the attacks are getting more and more sophisticated.

Imagine if a hacker could send a phishing SMS message directly to your phone, bypassing traditional mobile network defenses. The danger is that you may not even know you’re being attacked. So how does this type of attack work, and what can you do to protect yourself?
SMS Blaster: New Threat Bypasses Mobile Operators' Defenses
When Google warned smartphone users about a new threat called “SMS Blaster,” security experts knew this was no ordinary warning.
In fact, this attack method can silently bypass all defenses from mobile network operators, sending fraudulent messages directly to the victim's phone without going through the official telecommunications system.
What is SMS Blaster and how does it work?
Unlike traditional attacks that require phone number information or exploit vulnerabilities on the platform, SMS Blaster attacks use fake mobile transmission stations (also known as fake BTSs) that simulate a legitimate mobile transmission station to trick smartphones into connecting directly.
To send messages, the trick of the scammer is to create a fake BTS station. This station is the size of a suitcase, can cover about 2km and send thousands of messages at the same time.
Fake BTS stations will interfere with 3G, 4G signals around the network operator's BTS station, then broadcast at high power, causing mobile devices within the coverage area to receive messages. This is also the reason why many people in the same area will receive similar messages.
Accordingly, the waves of fake BTS stations will overlap the network operator's waves. Within a distance of 100m, mobile devices will connect to the waves of fake BTS stations instead of connecting to the network operator. The content of the messages can be accompanied by online gambling websites or impersonating bank websites to commit fraud.
Fake BTS stations can overwhelm any phone within range, downgrade the network to 2G and send messages as intended. These fake BTS stations are often smuggled into Vietnam, the equipment is very compact so authorities have difficulty in checking and detecting.
This renders any anti-spam filters, spoofing blocks, or authentication measures from your carrier useless. The victim can receive messages as if they came from a legitimate source, while in reality they are being tracked, scammed, or exploited for personal data.
Not only that, SMS blaster attacks do not target specific phone numbers. Instead, hackers target geographic areas where there is a high likelihood of “potentially rich” users, such as high-end residential areas or financial centers, where many people own expensive devices and valuable accounts.
Why is 2G a “back door” for hackers?
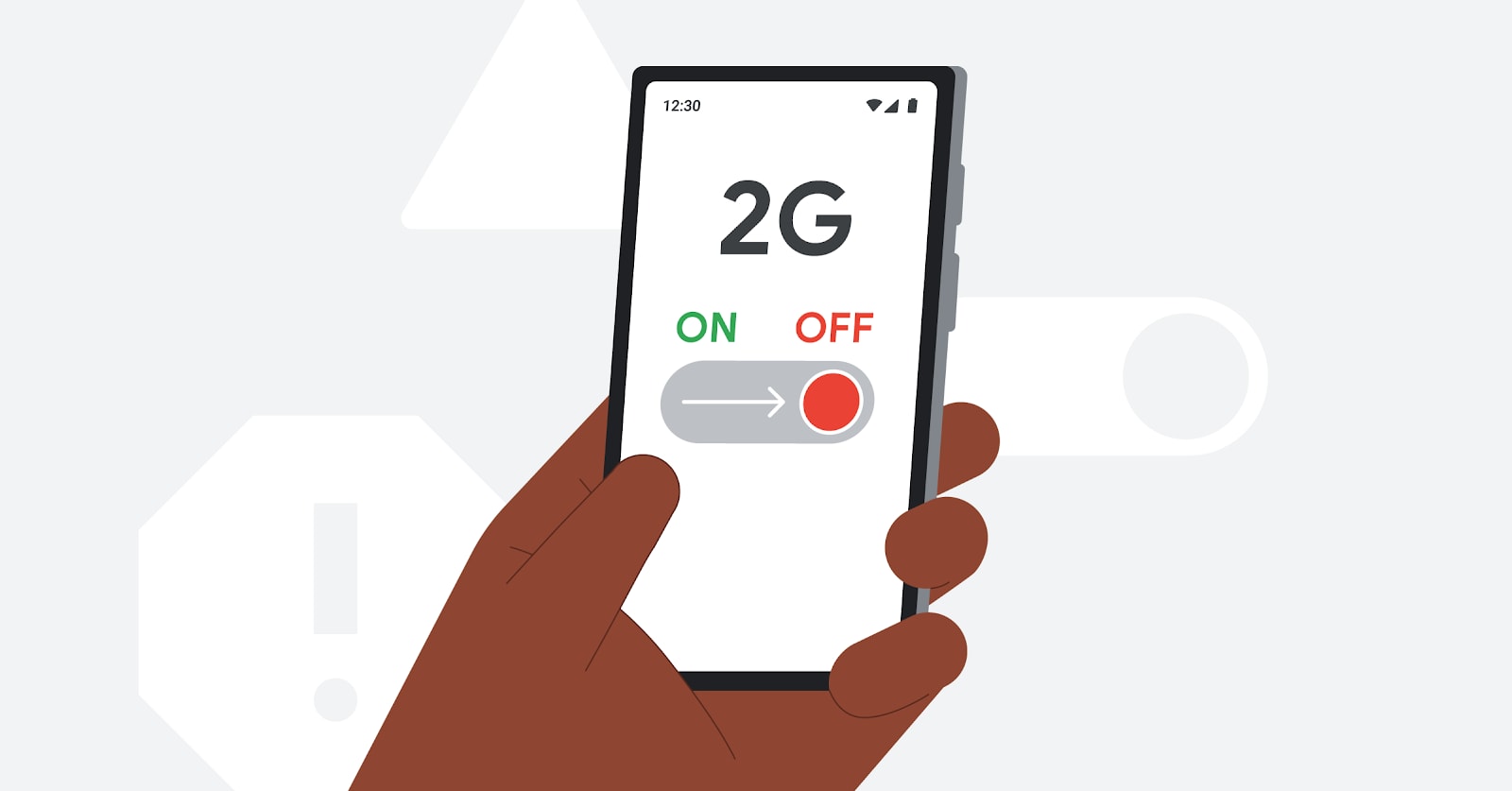
The first step to preventing this type of attack, according to Google, is to turn off your phone's 2G network connection. 2G networks, which were introduced in the 1990s, are not designed to protect against modern threats. Weak encryption techniques and the ability to be easily intercepted make them a serious vulnerability that hackers can exploit.
In most of the cases of spreading fake BTS messages in Vietnam, attackers take advantage of the weak security mechanism of the 2G (GSM) network, which does not require authenticating the BTS station with the terminal device, and the phone's operating mechanism of always connecting to the station with the strongest signal. From these two factors, the attacker can perform a Machine in the Middle (MitM) attack by placing a fake BTS between the phone's connection and the real BTS station.
Even if you live in an area that has discontinued 2G support, your device can still be tricked into connecting to a rogue cell tower if 2G is not completely disabled.
How to turn off 2G on Android and iPhone
To turn off 2G on smartphones using Android 16, go toSetting>Security & Privacy>Advanced protection> Enable featureDevice protection.
When enabled, the feature will monitor for suspicious activity, automatically limit USB connections to charging only when locked, force the device to restart after 72 hours if locked, and most notably, completely block calls using 2G networks (except in emergency situations).
For iPhone users, there is currently no option to turn off 2G separately in the standard settings. The only way is to enable it.Lockdown Mode, an enhanced security mode designed for people at risk of being targeted, such as journalists, activists, or high-profile business people. When enabled, this mode severely limits the device's functionality to minimize the possibility of exploitation.
Warnings from real arrests
Recently, the Radio Frequency Department (Ministry of Science and Technology) has coordinated with professional units under the Ministry of Public Security and mobile network operators to arrest dozens of subjects using fake BTS stations for the purpose of spreading spam and scam messages, especially in densely populated areas such as Hanoi and Ho Chi Minh City.

Although the subjects used sophisticated tricks such as using new types of fake BTS stations, installing them on cars and motorbikes and frequently traveling through many routes, they were all quickly discovered and arrested in a short time.
Not only in Vietnam, but this fraud method has also taken place in many countries around the world such as China, the UK, etc., along with evidence showing that attackers are exploiting vulnerabilities in mobile communication standards, specifically using devices that simulate broadcast stations to fool terminals.
Beware of warning signs of fraud on smartphones
While SMS Blaster is a serious threat, the most common type of attack over the past month was still the familiar phishing scam, according to a new report from security firm Trend Micro. The subjects impersonated major brands such as PayPal, Netflix, Toyota or Google to send messages or emails to steal user information.
“Whether online or in real life, the golden rule remains: if something sounds too good to be true, it almost certainly isn't,” warns Trend Micro.
As text message scams become more sophisticated, Trend Micro warns users to be especially wary of “unexpected contact” situations. According to the security firm, reputable organizations rarely or almost never ask you to provide personal or financial information via text message, especially if you have no previous contact with them.
Another telltale sign is spelling or grammar errors. If the message content looks sloppy, clunky, or unprofessional, that could be a red flag. Legitimate companies often have strict controls over the quality of information they send to customers, especially when it comes to financial or service-related messages.
Also, always ask yourself, “Is this message about me?” If you’re not expecting a delivery, the package notification is fake. If you’ve never entered a sweepstakes, the prize offer is probably a scam. Likewise, if you haven’t purchased a gift card from a retailer, a message mentioning one is probably a scam.
Google is also now stepping up protections for Google Pixel smartphone users, with plans to integrate features likeFraud Detection(Scam Detection) and andCall filtering(Call Screen) right from the device setup step, to help users proactively identify and prevent security risks from the beginning.






