Computer data can be lost with just 1 MS Word file
2016 is witnessing a strong comeback of many types of ransomware and even more dangerous when crypto-ransomware (encrypting user data to demand ransom) accounts for the majority of infections in recent times.
Recently, cybersecurity experts have continued to discover a new type of ransomware called Locky, which uses the AES encryption algorithm to encrypt data and files on network sharing. The way this ransomware infects and spreads over the Internet is also surprisingly simple: Microsoft Word.
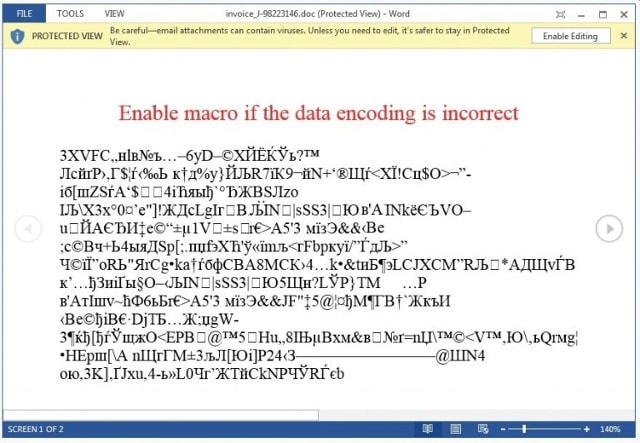 |
| Your computer will be encrypted when you enable macros to view Word file contents. |
Specifically, Locky will hide under a Word file with a malicious macro attached and spread through emails that impersonate payment invoices, sales contracts or contain curious content. When the email recipient activates the macro to view the content in this Word file, it will silently download Locky from the hacker's server and immediately perform the process of encrypting all files on the compromised computer.
This ransomware will scan the entire hard drive and even network shares to identify the encrypted files. However, it will ignore system files/folders such as tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot and Windows to ensure that users can still boot Windows normally.
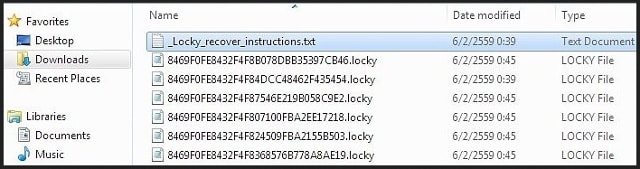 |
All files after being encrypted by AES algorithm will be renamed to [unique_id][identifier].locky. More sophisticated, Locky will delete all System Restore information so that users have no other way to restore their data.
Finally, the malware changes the desktop wallpaper to an image that warns victims of what has happened to their data, along with links to a decryption page and demands a ransom of around 0.5 bitcoin (more than $200) to restore their files. They have only two options: either reinstall the entire system, accept the loss of data, or bitterly pay the hacker.
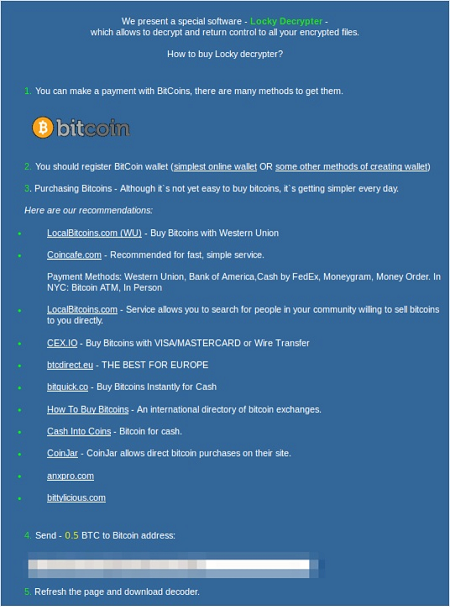 |
| Pay ransom (bitcoin) or accept losing all data? |
In fact, Locky still inherits the same techniques as other previously discovered ransomware, such as the ability to completely change the file name for encrypted files to make it difficult to recover data - similar to Cryptolocker. However, it is more dangerous with the ability to encrypt data even on Network Sharing - a threat to large computer systems.
Security company Kaspersky has had to admit that, if victims have fallen into this situation, they can do nothing but pay the hackers a ransom - as what Hollywood Presbyterian Hospital did yesterday: paying $17,000 in bitcoin in exchange for peace.
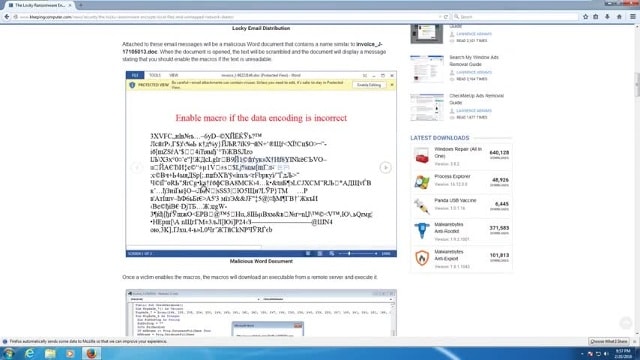 |
| What Locky does on the user's computer. |
Currently, this ransomware is still spreading at a rate of 4,000 new infections per hour, approximately 100,000 per day in Germany, the Netherlands, the US, Croatia, Mexico, Finland... It is puzzling that in 2016, a Word file can encrypt all of a user's data!
According to Tri Thuc Tre
| RELATED NEWS |
|---|






.jpg)
